Implementing Effective Security Measures
Set up a policy framework based on your organisation’s operational needs. Identify the assets to protect - personnel, information, physical assets, and services - that are necessary for ongoing operations or the national interest. Conduct a risk assessment using Business Impact Levels (BILs) to inform the policies, plans, and processes. Consider other operational policies and outcomes that could be affected. Record the policies, plans, and processes in one document or separate documents (but coordinate their development). Make sure the whole organisation is aware of the security policies, plans, and processes by publishing them on the intranet and promoting them. Security Awareness Training provides more information. Review them regularly, at least every two years, to identify gaps and keep up with changes to risk factors.
The Below shows how your policies, plans and processes interlink and are informed by your risk assessment.
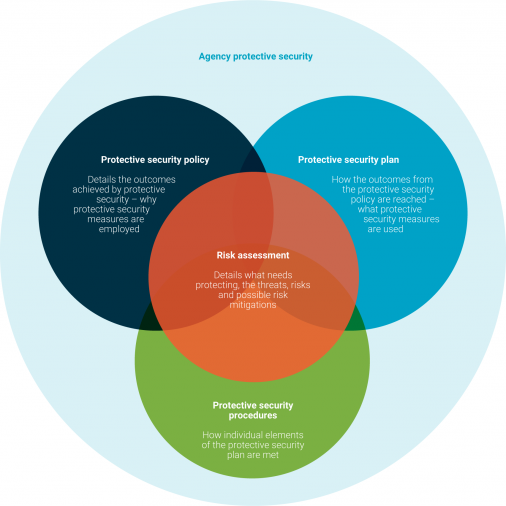
Create security policy that covers governance, personnel, information, and assets
Your Protective Security Policy provides a mandate for your organisation’s protective security plan and processes, meeting the Mandatory Requirements security system
The Chief Executive/Agency Head, or their delegate, must approve the Protective Security Policy and ensure its enforcement. The Chief Security Officer (or CSO) should actively monitor the policy.
The policy must cover four key areas: Governance, Personnel, Information, and Protection. Each policy should explain why it is necessary and who authorised it.
Governance arrangements
Governance arrangements outline how protective security relates to other operational governance components, such as:
- Employee and public safety
- Security requirements in contracts
- Assigning security management roles
- Business Impact Levels (BILs)
- Audit and compliance reporting
- Fraud risk management
- Sourcing and handling foreign government information
- Processes for policy exceptions
- Review and amendment processes
Personnel security policy
Ensure your personnel security policy includes:
- Employee and contractor security checks
- Security clearance requirements, including managing clearances
- Emergency access to confidential materials
- Procedures to investigate and manage security incidents.
Physical security policy
Your physical security policy should address:
- Access to your facilities by your people, visitors, and children - you may need site-specific policies if different facilities have different roles or risks.
- The security and safety of your people - ensure your security policy corresponds with your other safety policies.
- Working away from your office.
- The physical security of your information.
Develop your security plan and processes
Your organization’s protective security plan and processes must reduce security risks while allowing secure information sharing. These processes may be part of your security plan, or stand-alone advice for staff.
Your plan should be comprehensive and detailed. Consult with staff from all sections of your organization, including the Chief Security Officer, Chief Information Security Officer, Health & Safety Manager, Information Technology Security Manager, Privacy Officer, property managers, and security manager/advisors. Get senior management’s support to ensure the plan’s success.
The objectives of a security plan are to use risk assessments to identify areas of security risk and outline practical steps to minimize them. Develop separate site security plans for each of your sites. Consider carefully how you classify and protect the security plan and the business impact if the plan’s confidentiality is compromised. Classify individual elements of the plan as appropriate.
Your security plan must cover four key areas: security of governance, personnel, information, and physical assets.
Governance arrangements
Governance arrangements should include:
- Defining roles and responsibilities for security
- Contracting service providers and third-party security
- Planning for business continuity and disaster recovery
- Increasing security in response to threats
- Reporting incidents and conducting investigations
- Audit and compliance reporting
- Fraud risk management
- Reviewing and amending plans.
If governance arrangements are managed in standalone plans by other sections of your organisation, be sure to consult your security management personnel while developing individual plans.
Personnel security arrangements
Personnel security should include:
- Recruitment provisions in collaboration with Human Resource Management
- Police verification and clearance
- Contact reporting
- Security clearance management
- Ongoing security awareness training.
Physical security arrangements
Physical security measures should include:
- Creating site security plans
- Ensuring the safety of personnel, visitors and the public
- Securing information
- Protecting physical assets
- Implementing access control systems
- Installing security alarms
- Securing disaster recovery and alternative sites, and establishing business continuity plans
- Establishing physical security for remote work and work away from the office.
