The surveillance cameras captured everything. A warehouse worker, employed for just three months, systematically removing high-value electronics from incoming shipments. The theft went undetected for weeks—not because the security system failed, but because the perpetrator had legitimate access, knew the blind spots, and understood exactly when supervisors made their rounds.
This isn't a hypothetical scenario. It's happening in logistics facilities across India every day.
While companies invest heavily in perimeter security, advanced locks, and sophisticated alarm systems to keep threats out, the most dangerous security risks are already inside—wearing company uniforms and carrying access cards.
The Uncomfortable Truth About Insider Threats
Recent industry analysis reveals a sobering reality: a significant portion of security incidents, including theft, can be attributed to internal sources. This includes employees, contractual staff, drivers, and other personnel with legitimate access to facilities or goods.
The numbers are startling when you consider the scale:
- India's logistics sector employs millions across various skill levels
- The industry faces chronic skilled labor shortages
- High attrition rates create constant recruitment pressure
- Rapid expansion often leads to rushed hiring decisions
Why Insider Threats Are the Perfect Storm
Unlike external threats that must overcome physical barriers and security systems, insider threats come with built-in advantages:
Legitimate Access: They're supposed to be there, making their presence unremarkable System Knowledge: They understand security procedures, shift patterns, and vulnerable windows Trust Factor: Colleagues and supervisors naturally trust authorized personnel Time Advantage: They can plan and execute thefts over extended periods Evidence Challenges: Internal theft can be harder to detect and prove
The Real Cost: Beyond Missing Inventory
When companies calculate the impact of insider threats, they often focus solely on stolen goods. But the true cost extends far beyond missing inventory:
Direct Financial Losses
- Stolen merchandise: High-value electronics, pharmaceuticals, luxury goods
- Damaged goods: Improper handling during theft attempts
- Contaminated products: Particularly critical in cold chain operations
Operational Disruption
- Investigation downtime: Operations slow while incidents are investigated
- System overhauls: Implementing new security measures mid-operation
- Staff replacement: Recruiting and training replacement personnel
- Morale impact: Remaining staff feeling surveilled and distrusted
Long-term Business Impact
- Insurance premium increases: Poor security records drive up costs
- Client relationship damage: Major customers demand security guarantees
- Reputation harm: Word spreads quickly in industry networks
- Compliance issues: Regulatory scrutiny following security incidents
The Indian Logistics Context: Why the Risk Is Higher
Several factors make insider threats particularly challenging in India's current logistics environment:
Rapid Industry Growth
The pressure to scale operations quickly often compromises thorough screening:
- Rushed recruitment: Positions filled quickly to meet operational demands
- Insufficient verification: Background checks that don't dig deep enough
- Inadequate training: New hires starting work before proper security orientation
Skills Shortage Crisis
A chronic shortage of skilled logistics personnel creates additional risks:
- Compromised standards: Accepting candidates who might not meet ideal criteria
- Limited options: Fewer qualified candidates to choose from
- Competitive pressure: Companies competing for the same talent pool
Unorganized Sector Challenges
Parts of the logistics ecosystem still lack standardized practices:
- Inconsistent screening: Different standards across the supply chain
- Documentation gaps: Incomplete or unreliable employment records
- Compliance variations: Inconsistent adherence to labor laws and regulations
Red Flags: Early Warning Signs of Insider Threats
Successful insider threat prevention starts with recognizing warning signs before incidents occur:
Behavioral Indicators
Financial Stress Signs
- Discussions about money problems or debt
- Lifestyle changes that don't match salary levels
- Requests for salary advances or loans
Access Pattern Changes
- Working unusual hours without clear business reasons
- Accessing areas outside normal job responsibilities
- Staying late when others have left
Attitude Shifts
- Sudden disengagement from work or colleagues
- Complaints about company policies or treatment
- Defensive behavior when questioned about activities
Operational Red Flags
Inventory Discrepancies
- Unexplained shortages in specific areas or shifts
- Pattern of "errors" associated with particular individuals
- Delayed reporting of missing items
Procedure Violations
- Consistent failure to follow established protocols
- Attempts to bypass security measures
- Encouraging others to ignore procedures
Documentation Issues
- Incomplete or altered paperwork
- Missing signatures or authorizations
- Reluctance to provide required documentation
Technology Solutions: Your Digital Defense System
Modern technology provides powerful tools for detecting and preventing insider threats:
AI-Powered Video Analytics
Behavioral Analysis
- Detection of unusual movement patterns
- Identification of activities in restricted areas
- Recognition of suspicious interactions with inventory
Real-Time Alerts
- Immediate notification of policy violations
- Automated incident documentation
- Integration with access control systems
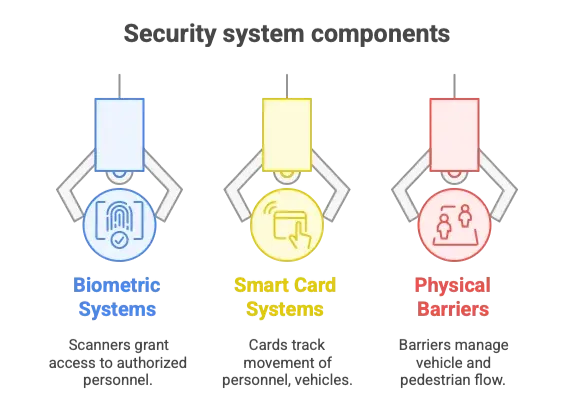
Advanced Access Control Systems
Biometric Authentication
- Fingerprint scanners for secure area access
- Facial recognition for visitor management
- Iris scanners for high-security zones
Smart Card Integration
- RFID tracking of personnel movement
- Time and attendance correlation
- Automated access logging and analysis
Inventory Management Technology
Real-Time Tracking
- RFID and barcode scanning for complete visibility
- Automated discrepancy detection and reporting
- Integration with personnel access data
Data Analytics
- Pattern analysis to identify unusual activities
- Correlation between access logs and inventory changes
- Predictive modeling for risk assessment
Building an Insider Threat Prevention Program
Effective insider threat prevention requires a comprehensive approach combining technology, processes, and culture:
Phase 1: Robust Screening and Verification
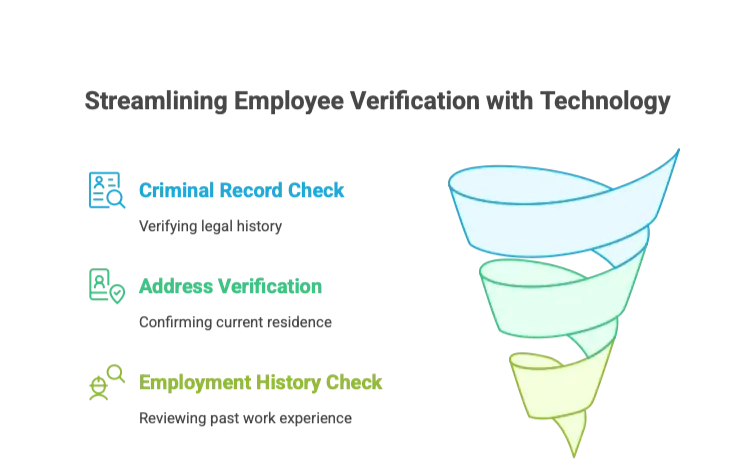
Comprehensive Background Checks
- Criminal record verification across multiple jurisdictions
- Employment history validation with previous employers
- Educational qualification verification
- Reference checks with professional and personal contacts
Address and Identity Verification
- Physical address confirmation through site visits
- Identity document authentication
- Family member and neighbor interviews where appropriate
Financial Background Review
- Credit history analysis for positions involving valuable goods
- Debt and financial stress indicators
- Previous bankruptcy or financial fraud history
Phase 2: Continuous Monitoring and Assessment
Ongoing Behavioral Monitoring
- Regular performance and conduct reviews
- Peer feedback and observation programs
- Anonymous reporting mechanisms for concerns
Technology-Enabled Oversight
- Access pattern analysis and anomaly detection
- Integration of security systems with HR data
- Automated flagging of unusual activities
Periodic Re-verification
- Annual background check updates for critical positions
- Random drug and alcohol testing programs
- Financial disclosure requirements for high-risk roles
Phase 3: Creating a Security-Conscious Culture
Comprehensive Training Programs
- Security awareness training for all personnel
- Specific insider threat recognition training for supervisors
- Regular updates on emerging threats and prevention techniques
Clear Policies and Procedures
- Written security policies accessible to all staff
- Clear consequences for security violations
- Regular communication about security importance
Positive Security Culture
- Recognition programs for security compliance
- Employee involvement in security improvement suggestions
- Open communication about security concerns
Legal and Ethical Considerations
While implementing insider threat prevention measures, companies must balance security needs with legal and ethical obligations:
Privacy Rights
- Ensure monitoring activities comply with privacy laws
- Obtain proper consent for surveillance and monitoring
- Limit data collection to legitimate business purposes
Employment Law Compliance
- Follow proper procedures for disciplinary actions
- Ensure fair treatment regardless of background or status
- Maintain confidentiality of investigation findings
Data Protection
- Secure storage of personal and background check information
- Limited access to sensitive employee data
- Regular deletion of outdated information
Case Study: Turning Vulnerability into Strength
Consider a major e-commerce fulfillment center that experienced significant internal theft. Instead of simply tightening security, they implemented a comprehensive insider threat prevention program:
Technology Investment
- AI-powered surveillance with behavioral analytics
- Biometric access control throughout the facility
- Real-time inventory tracking with automated alerts
Process Improvements
- Enhanced screening procedures with third-party verification
- Regular access reviews and privilege adjustments
- Anonymous reporting system for security concerns
Culture Change
- Security awareness training for all employees
- Recognition programs for security compliance
- Open communication about security importance
Results: Theft incidents dropped by 80% within six months, while employee satisfaction actually increased due to the fair and transparent security approach.
The ROI of Insider Threat Prevention
Investing in comprehensive insider threat prevention delivers measurable returns:
Direct Cost Savings
- Reduced theft losses: Immediate impact on bottom line
- Lower insurance premiums: Better security records reduce costs
- Decreased investigation costs: Fewer incidents mean fewer expensive investigations
Operational Benefits
- Improved efficiency: Streamlined security processes reduce operational friction
- Better inventory accuracy: Real-time tracking improves operational planning
- Enhanced reputation: Strong security attracts better clients and partners
Long-term Value
- Competitive advantage: Security becomes a differentiator in client proposals
- Scalability confidence: Secure operations enable confident expansion
- Regulatory compliance: Proactive security reduces compliance risks
Your Action Plan: From Vulnerable to Vigilant
Ready to protect your operations from insider threats? Here's your step-by-step implementation guide:
Immediate Steps (Next 30 Days)
- Audit current screening processes: Review existing background check procedures
- Assess technology gaps: Evaluate surveillance and access control systems
- Train management: Educate supervisors on insider threat warning signs
- Establish reporting mechanisms: Create channels for security concerns
Short-term Implementation (1-3 Months)
- Enhance screening procedures: Implement comprehensive verification processes
- Deploy monitoring technology: Install AI-powered surveillance and access control
- Develop policies: Create clear security policies and procedures
- Begin training programs: Start security awareness education for all staff
Long-term Strategy (3-12 Months)
- Integrate systems: Connect security technology with operational systems
- Build security culture: Embed security consciousness throughout the organization
- Measure and improve: Establish metrics and continuous improvement processes
- Expand protection: Apply lessons learned to new facilities and operations
The Bottom Line: Trust But Verify
Insider threats represent one of the most significant security challenges facing India's logistics sector. But companies that take a proactive, comprehensive approach to prevention can turn this vulnerability into a competitive advantage.
The key is balancing trust with verification, technology with human judgment, and security with operational efficiency. Companies that get this balance right don't just prevent theft—they create more secure, efficient, and trustworthy operations that attract better clients, better employees, and better business outcomes.
Your employees should be your greatest asset, not your greatest risk.
Ready to transform your approach to insider threat prevention? Our comprehensive industry analysis includes detailed frameworks for employee verification, technology implementation strategies, and proven methodologies for building security-conscious cultures.
Download the Complete Security Analysis →
Get access to detailed insider threat prevention frameworks, technology evaluation criteria, implementation timelines, and cost-benefit analysis tools.
Need help implementing an insider threat prevention program at your facility? Our security experts can conduct a confidential assessment of your current vulnerabilities and develop a customized prevention strategy.
Schedule a Confidential Security Assessment →
Related Reading
- Why India's Booming Logistics Sector Faces a Security Crisis: Understanding the broader security landscape
- Coming Next: [How AI and smart technology are revolutionizing warehouse security](/blog/ from-reactive-to-proactive-how-ai-and-smart-technology-are-revolutionizing-warehouse-security)





