Cold Chain to E-commerce: Why Different Logistics Segments Need Specialized Security Approaches
The alarm went off at exactly 3:15 AM. But this wasn't a typical security breach—the temperature in the pharmaceutical cold storage had risen by just 2°C above the acceptable range. Within minutes, the integrated security system had:
- Locked down access to the affected zone
- Alerted the security team and facility manager
- Initiated backup cooling protocols
- Documented the incident for regulatory compliance
- Identified the last person to access the area using biometric logs
For a cold chain facility, this 2°C deviation could have meant the difference between life-saving medicines and worthless inventory.
This scenario illustrates a crucial reality: logistics security isn't one-size-fits-all. A security approach that works perfectly for an e-commerce fulfillment center could be completely inadequate for a pharmaceutical cold chain facility, and vice versa.
As India's logistics sector diversifies across multiple specialized segments—each with unique operational requirements, regulatory constraints, and risk profiles—the need for segment-specific security strategies has never been more critical.
The Diversification Reality: Why Generic Security Fails
India's logistics sector has evolved far beyond simple warehouse storage. Today's ecosystem includes:
- E-commerce fulfillment centers processing millions of orders daily
- Cold chain facilities maintaining critical temperature controls
- Grade-A warehouses serving multinational corporations
- Manufacturing-linked storage handling specialized industrial materials
- Third-party logistics hubs managing diverse client requirements
- Automotive parts distribution with just-in-time delivery pressures
- Pharmaceutical logistics under strict regulatory oversight
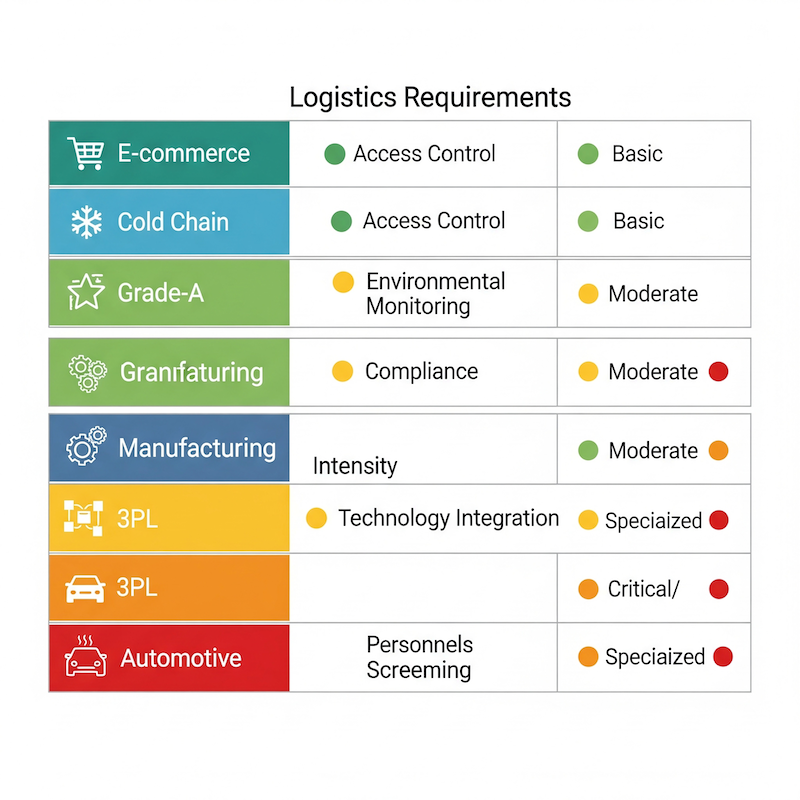
Each segment operates under different pressures, faces unique threats, and requires specialized security measures that align with their operational realities.
The Cost of Misaligned Security
Over-Engineering Consequences:
- Unnecessary costs from sophisticated systems where basic security suffices
- Operational friction from complex procedures that don't match workflow needs
- Staff resistance to security measures that seem irrelevant to their work
- Resource waste deploying expensive technology without clear ROI
Under-Engineering Risks:
- Regulatory violations in compliance-sensitive segments
- Catastrophic losses when basic security fails to protect high-value operations
- Client contract breaches when security doesn't meet industry standards
- Reputation damage from incidents that specialized security could have prevented
E-commerce Fulfillment: Speed, Scale, and Smart Security
E-commerce fulfillment centers face unique challenges that traditional warehouse security wasn't designed to handle:
Operational Characteristics
- High-velocity processing: Thousands of orders per hour during peak periods
- Diverse inventory: Electronics, fashion, books, household items in one facility
- Seasonal fluctuations: 300-500% volume increases during festive periods
- Multiple touchpoints: Pick, pack, sort, dispatch with numerous handling stages
- Reverse logistics: Returns processing with unknown product conditions
Specialized Security Requirements
Scalable Access Control E-commerce facilities need security systems that can accommodate:
- Seasonal workforce expansion from 500 to 2,000+ employees
- Multiple shift patterns including overnight processing
- Temporary worker integration with limited facility access
- Visitor management for carrier pickups and vendor services
Zone-Based Security Architecture
- Receiving areas: Basic access control with inventory verification
- High-value storage: Electronics and luxury items require biometric access
- Picking zones: Real-time inventory tracking with theft detection
- Packing areas: Process monitoring to prevent substitution fraud
- Dispatch zones: Secure loading with carrier verification
Technology Integration
- Warehouse Management System integration linking security with order processing
- Real-time inventory tracking preventing diversion during fulfillment
- AI-powered video analytics detecting unusual picking behaviors
- Mobile device management securing handheld scanners and devices
E-commerce Security Success Story
Challenge: A major e-commerce player was experiencing 2-3% inventory shrinkage during peak season processing.
Solution: Implemented zone-based security with:
- Bio metric access control for high-value areas
- AI surveillance during picking operations
- Real-time inventory reconciliation
- Enhanced seasonal worker screening
Results:
- Shrinkage reduced to 0.3% during next peak season
- ₹4.2 crore annual savings in prevented losses
- 25% faster processing due to streamlined security workflows
- 95% improvement in inventory accuracy
Cold Chain Logistics: Where Security Meets Science
Cold chain facilities present some of the most complex security challenges in logistics, where security breaches can literally be matters of life and death:
Critical Success Factors
- Temperature integrity: Maintaining 2-8°C for vaccines, -18°C for frozen foods
- Contamination prevention: Preventing any compromise to product sterility
- Regulatory compliance: Meeting FDA, WHO, and local pharmaceutical standards
- Chain of custody: Complete documentation of every product interaction
- Emergency protocols: Rapid response to equipment failures or power outages
Specialized Security Architecture
Environmental Security Integration
- Temperature monitoring systems with security access correlation
- Backup power security ensuring cooling continues during outages
- Environmental alert integration triggering security protocols during deviations
- Clean room protocols maintaining sterility while enabling security monitoring
Enhanced Personnel Screening
- Health certification requirements beyond standard background checks
- Specialized training verification on handling sensitive products
- Continuous health monitoring ensuring staff fitness for clean room work
- Restricted access protocols limiting personnel to qualified individuals only
Advanced Documentation Systems
- Blockchain-based tracking creating immutable records of product handling
- Bio metric correlation linking every product interaction to specific individuals
- Real-time compliance reporting automatically generating regulatory documentation
- Exception management immediate alerts for any deviation from protocols
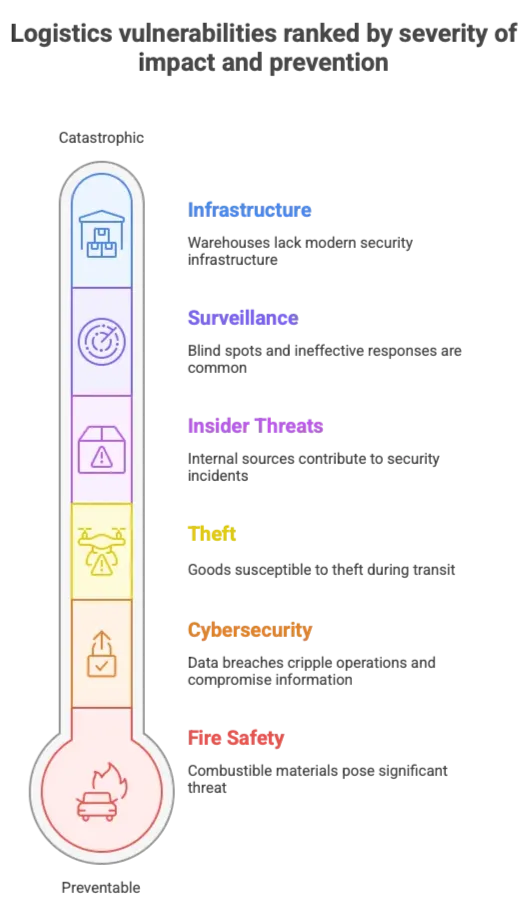
Regulatory Compliance Integration
Pharmaceutical Standards
- GDP (Good Distribution Practice) compliance with full audit trails
- Temperature mapping validation with security oversight
- Qualification protocols for all staff handling pharmaceutical products
- Deviation management systematic handling of any compliance exceptions
Food Safety Requirements
- HACCP compliance with security measures supporting food safety
- Traceability requirements linking security data with product tracking
- Contamination prevention protocols integrated with access control
- Recall support rapid identification of affected products and personnel
Grade-A Warehousing: Premium Security for Premium Clients
Grade-A warehouses serve multinational corporations and major domestic companies that demand enterprise-level security standards:
Client Expectations
- Corporate security standards matching international best practices
- Transparent reporting with detailed security metrics and incident documentation
- Professional presentation reflecting positively on client brands
- Scalable services supporting business growth and changing requirements
- Technology leadership demonstrating innovation and reliability
Enterprise-Level Security Features
Comprehensive Surveillance Ecosystem
- HD IP cameras with facial recognition and behavior analytics
- Perimeter intrusion detection with multiple layers of protection
- Vehicle tracking systems monitoring all on-site transportation
- Visitor management platforms with photo ID and background verification
- Integration capabilities connecting with client security systems
Advanced Access Management
- Multi-factor authentication combining cards, biometrics, and PINs
- Time-based access control automatically adjusting permissions by schedule
- Segregated storage areas with client-specific access restrictions
- Audit trail generation providing detailed access reports for client review
- Emergency override protocols maintaining security during crisis situations
Professional Security Services
- Trained security personnel with corporate communication skills
- 24/7 command center operations with professional monitoring
- Incident response protocols designed for high-stakes environments
- Regular security assessments proactively identifying and addressing vulnerabilities
- Client communication systems providing transparent security updates
Grade-A Success Metrics
A Fortune 500 consumer goods company selected a Grade-A facility based on security capabilities:
Security Requirements Met:
- Zero security incidents in 18 months of operation
- 99.98% system uptime for all security technology
- Sub-30-second response time to all security alerts
- Complete audit trail documentation for all facility access
- Integration with client's global security monitoring system
Business Impact:
- ₹12 crore inventory stored with zero losses
- Passed 3 unannounced client security audits
- Enabled expansion of client's India operations
- Became reference site for additional client facilities
Manufacturing-Linked Warehousing: Industrial Security Protocols
Manufacturing-linked storage facilities require security approaches that understand industrial operations and specialized materials:
Unique Operational Requirements
- Raw material security protecting expensive industrial inputs
- Work-in-progress protection securing partially completed products
- Finished goods staging maintaining quality until shipment
- Equipment security protecting valuable machinery and tools
- Intellectual property protection securing proprietary processes and designs
Industrial Security Specialization
Material-Specific Protocols
- Hazardous material handling with specialized containment and monitoring
- High-value component security for electronics and precision parts
- Bulk material management securing large quantities of raw materials
- Quality control integration ensuring security doesn't compromise production standards
- Just-in-time coordination balancing security with production scheduling needs
Process Integration Security
- Production line security monitoring manufacturing processes
- Quality checkpoint integration combining security with quality assurance
- Shift change protocols maintaining security during personnel transitions
- Maintenance access control securing facilities during equipment service
- Emergency shutdown procedures protecting assets during crisis situations
Third-Party Logistics: Multi-Client Security Management
3PL providers face the complex challenge of maintaining security across multiple clients with different requirements:
Multi-Client Challenges
- Segregated storage requirements keeping different clients' goods separate
- Varying security standards meeting different client specifications
- Shared facility management maintaining security across multiple operations
- Cost allocation complexity fairly distributing security costs among clients
- Scalability requirements adapting to changing client needs
Flexible Security Architecture
Modular Security Design
- Configurable access zones adapting to different client requirements
- Scalable surveillance systems adjusting coverage based on client needs
- Flexible personnel deployment providing appropriate security levels
- Customizable reporting meeting diverse client documentation requirements
- Technology integration options connecting with various client systems
Client-Specific Protocols
Individual security agreements tailoring approaches to client needs
Dedicated security teams for high-requirement clients
Separate incident reporting maintaining client confidentiality
Custom training programs addressing specific client protocols
Independent audit capabilities supporting client compliance requirements
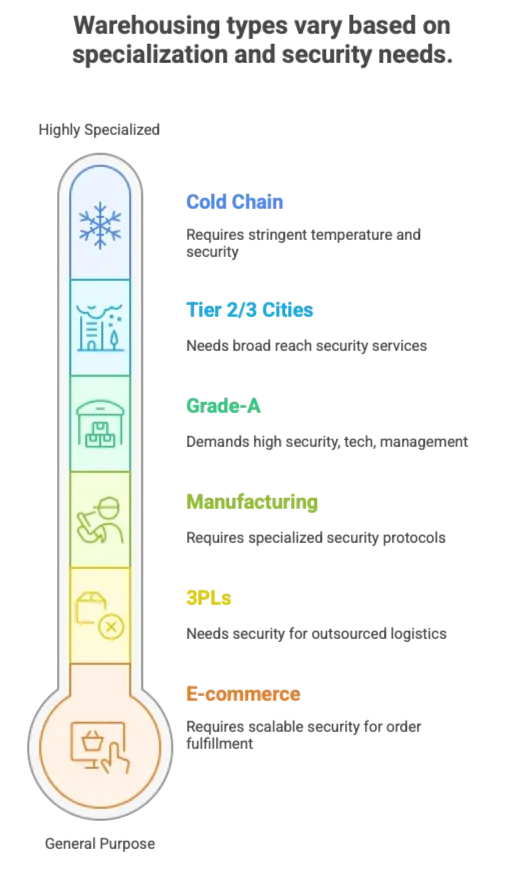
Automotive Logistics: Precision and Protection
Automotive parts distribution requires security approaches that understand just-in-time manufacturing and high-value components:
Industry-Specific Requirements
- Just-in-time delivery where security delays can shut down production lines
- High-value components like engines, transmissions, and electronic modules
- Serial number tracking for warranty and recall management
- Quality assurance integration ensuring parts meet manufacturing standards
- Supplier coordination managing security across complex supply chains
Automotive Security Solutions
Component-Level Tracking
- RFID and barcode integration tracking individual high-value parts
- Serial number verification ensuring authenticity and preventing counterfeiting
- Quality checkpoint security monitoring parts during inspection processes
- Packaging integrity monitoring detecting tampering during storage and transport
- Real-time location tracking providing precise component location data
Technology Enablers: Platforms That Scale Across Segments
Modern security technology platforms enable segment-specific customization while maintaining operational efficiency:
Unified Management Platforms
Configurable Security Orchestration
- Rule-based automation adapting responses to different segment requirements
- Multi-tenant architecture supporting diverse client needs in single platform
- API integration capabilities connecting with segment-specific systems
- Custom reporting engines generating appropriate documentation for each segment
- Scalable infrastructure supporting growth across all segments
Artificial Intelligence Applications
- Behavior pattern recognition learning normal operations for each segment
- Predictive analytics identifying risks specific to different logistics types
- Automated compliance monitoring ensuring adherence to segment regulations
- Anomaly detection identifying unusual activities in context of specific operations
- Performance optimization improving security efficiency across different segments
Implementation Strategy: Right-Sizing Security for Your Segment
Segment Assessment Framework
Step 1: Operational Characterization
- Volume and velocity analysis understanding processing requirements
- Value density evaluation assessing theft and loss risks
- Regulatory requirement mapping identifying compliance obligations
- Client expectation documentation understanding security service levels
- Risk profile development creating segment-specific threat models
Step 2: Security Architecture Design
- Technology selection choosing appropriate systems for segment needs
- Process integration planning ensuring security supports operations
- Personnel requirement analysis determining staffing and training needs
- Cost-benefit optimization balancing security investment with risk reduction
- Scalability planning designing for future growth and changes
Step 3: Implementation and Optimization
- Phased deployment minimizing operational disruption during implementation
- Performance monitoring measuring security effectiveness and efficiency
- Continuous improvement adapting security based on operational experience
- Client feedback integration incorporating stakeholder input for enhancement
- Regular assessment updates keeping security current with changing requirements
The Competitive Advantage of Specialized Security
Organizations that implement segment-appropriate security strategies gain significant competitive advantages:
Operational Excellence
- Reduced friction between security and operations
- Improved efficiency through optimized security processes
- Enhanced compliance meeting segment-specific requirements
- Better risk management addressing actual rather than theoretical threats
- Superior client service demonstrating understanding of client needs
Business Growth
- Premium pricing for demonstrated security expertise
- Client retention through superior security service delivery
- Market expansion into new segments with appropriate security capabilities
- Partnership opportunities with clients seeking specialized security providers
- Competitive differentiation standing out in crowded logistics markets
Future Evolution: Emerging Segments and Security Needs
As India's logistics sector continues to evolve, new specialized segments are emerging:
Healthcare and Medical Device Logistics
- Biomedical security protecting sensitive medical equipment
- Patient data protection securing health information during transport
- Sterility maintenance ensuring medical device integrity
- Emergency response supporting critical healthcare supply chains
E-waste and Reverse Logistics
- Data destruction security ensuring complete information elimination
- Material recovery optimization securing valuable recovered materials
- Environmental compliance meeting electronic waste regulations
- Chain of custody documentation for recycling and disposal
Luxury Goods and High-Value Items
- Enhanced authentication preventing counterfeit infiltration
- Discrete handling maintaining confidentiality for high-profile clients
- Insurance coordination supporting specialized coverage requirements
- Concierge-level service providing white-glove logistics security
Your Segment Security Strategy: Where to Start
Ready to optimize your security approach for your specific logistics segment? Here's your action plan:
Immediate Assessment (Next 30 Days)
- Segment characterization: Define your operational type and specific requirements
- Gap analysis: Compare current security with segment best practices
- Client expectation review: Understand security service level requirements
- Risk assessment: Identify segment-specific threats and vulnerabilities
Strategy Development (30-90 Days)
- Security architecture design: Create segment-appropriate security framework
- Technology evaluation: Select systems that match operational requirements
- Process integration planning: Ensure security supports rather than hinders operations
- Investment prioritization: Focus resources on highest-impact security improvements
Implementation Excellence (3-12 Months)
- Phased deployment: Implement security enhancements with minimal disruption
- Performance monitoring: Measure and optimize security effectiveness
- Stakeholder feedback: Incorporate client and operational input for improvements
- Continuous evolution: Adapt security as segment requirements change
The Bottom Line: Security as a Business Differentiator
In today's competitive logistics market, security isn't just about preventing losses—it's about enabling business success. Companies that understand their segment's unique security requirements and implement appropriate solutions don't just reduce risks; they create competitive advantages that drive growth, improve client relationships, and support premium pricing.
The question isn't whether you can afford to invest in segment-specific security. It's whether you can afford not to.
Ready to transform your security approach from generic to specialized? Our comprehensive industry analysis includes detailed security frameworks for every major logistics segment, technology selection guides, and implementation roadmaps.
Download the Complete Segment Security Guide →
Access segment-specific security frameworks, technology evaluation matrices, compliance checklists, and proven implementation strategies for all major logistics segments.
Need help developing a specialized security strategy for your logistics segment? Our security experts understand the unique requirements of different logistics operations and can develop customized solutions that enhance both security and operational efficiency.
Schedule a Segment Security Assessment →
Related Reading in This Series
- Why India's Booming Logistics Sector Faces a Security Crisis: Understanding the broader security landscape
- The Hidden Enemy: Insider Threats in Indian Logistics: Preventing internal security risks
- From Reactive to Proactive: AI Revolution in Warehouse Security: Technology solutions for modern security challenges
- The Manpower Crisis: Security Risks from Rapid Hiring: Workforce security strategies
- Coming Next: Future-proofing logistics security for emerging trends and technologies