At 2:47 AM, an AI system at a major e-commerce fulfillment center in Mumbai detected something unusual. A worker was lingering in the electronics section—not actively picking orders, just standing still for 47 seconds longer than the system's behavioral model predicted as normal. The AI cross-referenced this with the employee's access logs, shift schedule, and recent performance metrics. Within seconds, a security alert was generated, complete with video evidence and risk assessment.
What would have taken human security guards hours to notice and investigate was detected, analyzed, and reported in under 60 seconds.
This is the new reality of warehouse security in India—and it's just the beginning.
While traditional security systems wait for incidents to happen before responding, AI-powered solutions are preventing problems before they occur. The transformation is so significant that forward-thinking logistics companies are gaining competitive advantages not just in security, but in operational efficiency, cost reduction, and client confidence.
The Evolution: From Guards to Algorithms
Traditional warehouse security has remained largely unchanged for decades:
- Human patrols walking predetermined routes at set intervals
- Basic CCTV systems recording footage for post-incident review
- Simple alarm systems responding only to obvious breaches
- Manual processes for access control and incident reporting
But India's logistics sector is experiencing a technology revolution that's fundamentally changing how security works:
The AI Advantage: Why Machines See What Humans Miss
24/7 Vigilance Without Fatigue Human security guards naturally experience attention fatigue, especially during long shifts or quiet periods. AI systems maintain constant vigilance, processing video feeds, access logs, and sensor data simultaneously without ever losing focus.
Pattern Recognition at Scale While a human guard might monitor 4-6 camera feeds effectively, AI systems can simultaneously analyze dozens of video streams, identifying patterns and anomalies across vast facilities in real-time.
Predictive Capabilities Advanced AI doesn't just respond to incidents—it predicts them. By analyzing historical data, behavior patterns, and environmental factors, these systems can flag potential security risks before they materialize.
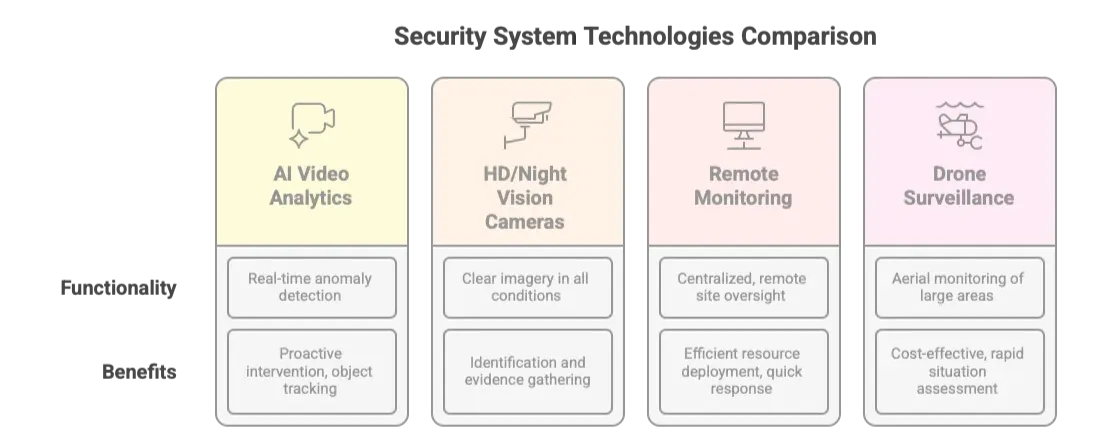
Smart Surveillance: Beyond Traditional CCTV
Modern warehouse surveillance has evolved far beyond simple video recording:
AI-Powered Video Analytics
Real-Time Behavioral Analysis
- Loitering detection: Identifying when individuals spend unusual amounts of time in specific areas
- Motion pattern analysis: Recognizing abnormal movement patterns or routes
- Object recognition: Detecting when items are moved or removed from designated areas
- Crowd behavior monitoring: Analyzing group dynamics and identifying unusual gatherings
Automated Incident Classification
- Theft detection: Recognizing concealment behaviors and unauthorized item removal
- Safety violations: Identifying unsafe practices like improper lifting or equipment misuse
- Access violations: Detecting unauthorized entry attempts or tailgating
- Emergency situations: Recognizing falls, medical emergencies, or safety hazards
Advanced Camera Technology
High-Definition and Night Vision Modern IP cameras provide crystal-clear imagery even in low-light conditions, enabling accurate identification and evidence collection. Features include:
- 4K resolution for detailed facial recognition and item identification
- Infrared night vision for 24/7 monitoring capability
- Pan-tilt-zoom functionality for comprehensive area coverage
- Weather-resistant housings for outdoor perimeter monitoring
Thermal Imaging Integration For specialized applications like cold chain monitoring, thermal cameras provide:
- Temperature monitoring for compliance verification
- Heat signature detection for security applications
- Fire prevention through early heat detection
- Energy efficiency monitoring by identifying thermal leaks
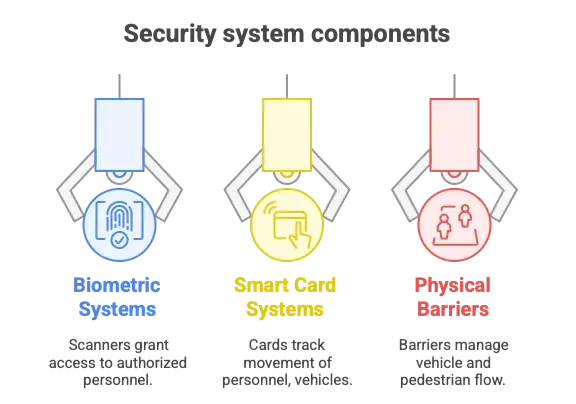
Access Control Revolution: Who Goes Where, When
Traditional lock-and-key systems are giving way to sophisticated access control solutions:
Biometric Authentication Systems
Fingerprint Recognition
- High accuracy with false acceptance rates below 0.001%
- Fast processing with sub-second authentication times
- Tamper resistance virtually impossible to duplicate or forge
- Comprehensive logging of all access attempts and timings
Facial Recognition Technology
- Contactless operation improving hygiene and user experience
- Real-time identification even in crowded environments
- Blacklist matching to prevent access by prohibited individuals
- Integration capabilities with existing security databases
Multi-Factor Authentication For high-security areas, combining multiple biometric factors:
- Fingerprint + facial recognition for critical storage areas
- Iris scanning + voice recognition for server rooms and administrative zones
- Behavioral biometrics analyzing typing patterns and gait recognition
Smart Card and RFID Systems
Advanced Access Management
- Time-based permissions automatically adjusting access based on shifts and schedules
- Zone-based restrictions limiting access to relevant work areas only
- Real-time tracking of personnel movement throughout facilities
- Integration with HR systems for seamless onboarding and termination processes
Vehicle Access Control
- RFID tags for trucks streamlining gate operations while maintaining security
- Driver identification linking vehicle access to verified drivers
- Load verification ensuring only authorized cargo enters/exits
- Visitor management temporary access for delivery personnel and contractors
Integrated Management Systems: The Security-Operations Connection
Modern Warehouse Management Systems (WMS) and Transportation Management Systems (TMS) are becoming powerful security tools:
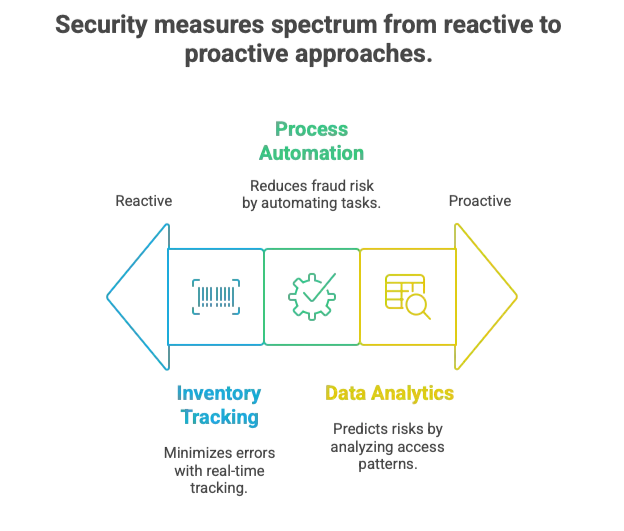
Real-Time Inventory Intelligence
Automated Discrepancy Detection
- Instant alerts when physical inventory doesn't match system records
- Pattern analysis identifying trends that might indicate systematic theft
- Location tracking knowing exactly where every item should be at all times
- Exception reporting highlighting unusual inventory movements
Predictive Loss Prevention
- Risk scoring for different inventory categories and locations
- Vulnerability mapping identifying high-risk areas and times
- Resource optimization deploying security resources where they're most needed
Process Automation Benefits
Reduced Human Error Automated systems eliminate many opportunities for mistakes that can create security vulnerabilities:
- Barcode scanning ensuring accurate inventory tracking
- Automated documentation reducing paperwork errors
- Digital workflows maintaining consistent processes across shifts
Enhanced Audit Trails Every action in modern systems creates digital records:
- Complete transaction histories for forensic analysis
- User activity logs tracking who did what and when
- System integration data correlating multiple data sources for comprehensive oversight
Cybersecurity: Protecting the Digital Infrastructure
As warehouses become increasingly connected, cybersecurity becomes as important as physical security:
Network Security Fundamentals
Segmented Networks
- Isolated security systems preventing lateral movement during breaches
- VPN access controls for remote monitoring and management
- Firewall configurations blocking unauthorized network access
- Regular security updates maintaining current protection levels
Data Encryption
- End-to-end encryption for sensitive communications
- Database security protecting employee and operational data
- Backup systems ensuring data availability during incidents
- Access logging monitoring who accesses what information
IoT Security Management
Device Authentication
- Unique device identities preventing unauthorized sensor access
- Certificate-based authentication ensuring only approved devices connect
- Regular security patching keeping IoT devices current with security updates
- Network monitoring detecting unusual device behavior
[Reference the "Strengthening Cybersecurity in Logistics" illustration showing data encryption, security audits, and employee training]
Employee Verification Technology: Digital Due Diligence
Technology is streamlining and enhancing employee screening processes:
Digital Background Verification
Automated Database Checks
- Criminal record searches across multiple jurisdictions
- Employment history verification with previous employers
- Educational qualification confirmation with institutions
- Reference verification through digital platforms
Continuous Monitoring
- Ongoing criminal record updates for existing employees
- Financial stress indicators for positions involving high-value goods
- Social media monitoring where legally permissible and relevant
- Behavioral change detection through integrated HR and security systems
Identity Verification Solutions
Document Authentication
- Digital document verification using OCR and validation databases
- Biometric document matching ensuring documents belong to the applicant
- Fraud detection algorithms identifying fake or altered documents
- Real-time verification reducing hiring delays
The ROI Revolution: Security That Pays for Itself
Modern security technology doesn't just prevent losses—it generates measurable returns:
Direct Cost Savings
Reduced Security Personnel Costs
- Fewer guards needed for routine monitoring tasks
- Optimized patrol routes based on AI-generated risk assessments
- Remote monitoring capabilities reducing on-site staffing requirements
Lower Insurance Premiums
- Risk reduction leading to insurance cost decreases
- Better incident documentation supporting claims and reducing disputes
- Proactive prevention demonstrating commitment to loss control
Operational Efficiency Gains
Faster Processing Times
- Automated access control reducing gate delays
- Streamlined inventory processes through integrated security and WMS
- Reduced investigation time with AI-generated incident reports
Improved Accuracy
- Fewer inventory discrepancies through automated tracking
- Reduced human error in security processes
- Better compliance documentation for regulatory requirements
Competitive Advantages
Client Confidence
- Transparent security reporting demonstrating operational reliability
- Reduced cargo insurance requirements for clients shipping through secure facilities
- Premium pricing potential for demonstrably secure operations
Scalability Support
- Technology-enabled expansion growing security capabilities with operations
- Standardized processes ensuring consistent security across multiple facilities
- Remote management enabling centralized oversight of distributed operations
Implementation Strategy: Your Technology Transformation Roadmap
Successful security technology implementation requires careful planning:
Phase 1: Assessment and Planning (30-60 Days)
Current State Analysis
- Security audit of existing systems and processes
- Vulnerability assessment identifying gaps and risks
- Technology inventory cataloging current security infrastructure
- ROI baseline establishing metrics for measuring improvement
Future State Design
- Technology selection based on specific operational needs
- Integration planning ensuring new systems work with existing infrastructure
- Budget allocation balancing investment with expected returns
- Timeline development realistic scheduling for implementation phases
Phase 2: Core System Implementation (3-6 Months)
Priority System Deployment
- Access control systems starting with highest-risk areas
- Video surveillance upgrade focusing on critical monitoring points
- Network infrastructure establishing secure, scalable connectivity
- Staff training ensuring effective use of new systems
Integration Testing
- System compatibility ensuring all components work together
- Performance testing validating system response times and reliability
- User acceptance testing confirming staff can effectively use new systems
- Security testing verifying systems meet security requirements
Phase 3: Advanced Features and Optimization (6-12 Months)
AI and Analytics Deployment
- Behavioral analytics implementing advanced threat detection
- Predictive modeling using historical data for risk prevention
- Automated reporting generating actionable security intelligence
- Continuous learning systems that improve over time
Process Integration
- Workflow automation connecting security systems with operations
- Data integration creating comprehensive operational dashboards
- Performance optimization fine-tuning systems based on actual usage
- Expansion planning preparing for growth and additional facilities
Real-World Success Stories: Technology in Action
Case Study: E-Commerce Giant's Transformation
A major Indian e-commerce company implemented comprehensive AI-powered security across 15 fulfillment centers:
Technology Deployed:
- AI video analytics with behavioral detection
- Biometric access control for 5,000+ employees
- Integrated inventory tracking with real-time alerts
- Centralized monitoring from Delhi command center
Results After 12 Months:
- 78% reduction in theft incidents
- 45% decrease in investigation time
- 30% improvement in inventory accuracy
- ₹2.3 crore annual savings in losses and operational costs
Case Study: Cold Chain Specialist's Innovation
A pharmaceutical logistics provider upgraded their temperature-controlled facilities:
Technology Solutions:
- Thermal imaging for cold chain compliance
- Environmental sensors with AI analysis
- Automated access logs correlated with temperature data
- Mobile alerts for all stakeholders
Business Impact:
- Zero temperature excursions in 8 months
- 25% reduction in compliance audit time
- 40% decrease in insurance premiums
- New client acquisition based on demonstrated reliability
Overcoming Implementation Challenges
Technical Challenges
Legacy System Integration
- Phased replacement rather than complete overhaul
- API development for connecting old and new systems
- Data migration preserving historical security information
- Parallel operation during transition periods
Staff Adaptation
- Change management addressing resistance to new technology
- Comprehensive training ensuring effective system utilization
- Ongoing support providing help during adaptation period
- Feedback integration improving systems based on user experience
Financial Considerations
Budget Management
- Phased investment spreading costs over time
- ROI tracking demonstrating value at each phase
- Financing options considering leasing vs. purchase
- Total cost of ownership including maintenance and upgrades
The Future: What's Coming Next
The technology revolution in warehouse security is accelerating:
Emerging Technologies
Advanced AI Capabilities
- Emotion recognition detecting stress or deception in personnel
- Predictive maintenance for security equipment
- Natural language processing for automated incident reporting
- Computer vision for quality control and compliance monitoring
IoT Integration
- Smart sensors throughout facilities providing comprehensive monitoring
- Wearable technology for personnel tracking and safety
- Environmental monitoring integrated with security systems
- Autonomous security robots for patrol and inspection duties
Industry Transformation
Standardization
- Industry-wide security protocols enabling seamless integration
- Certification programs for security technology providers
- Regulatory framework supporting technology adoption
- Best practice sharing across the logistics ecosystem
Your Next Move: Embracing the Technology Revolution
The question isn't whether AI and smart technology will transform warehouse security—it's whether your organization will lead or follow this transformation.
Companies that act now gain:
- First-mover advantages in technology adoption
- Competitive differentiation through superior security
- Cost advantages through early ROI realization
- Learning opportunities that inform future decisions
Those who wait risk:
- Higher implementation costs as technology becomes standard
- Competitive disadvantage against better-secured operations
- Increased incident exposure while maintaining outdated systems
- Client loss to providers offering demonstrably better security
Ready to Transform Your Security Operations?
The technology revolution in warehouse security represents the biggest operational improvement opportunity in decades. AI-powered systems, smart surveillance, advanced access control, and integrated management platforms aren't just preventing losses—they're enabling entirely new levels of operational efficiency and business growth.
The companies that successfully implement these technologies today will be the market leaders of tomorrow.
Want to understand exactly how these technologies can transform your specific operations?
Our comprehensive analysis includes detailed technology evaluation frameworks, implementation timelines, ROI calculators, and case studies from successful deployments across India's logistics sector.
Download the Complete Technology Implementation Guide →
Get access to vendor evaluation criteria, cost-benefit analysis tools, implementation checklists, and proven methodologies for technology-driven security transformation.
Ready to see these technologies in action at your facility? Our security technology experts can conduct a comprehensive assessment of your current systems and develop a customized implementation roadmap.
Schedule a Technology Assessment →
Related Reading in This Series
- Why India's Booming Logistics Sector Faces a Security Crisis: Understanding the broader security landscape
- The Hidden Enemy: Insider Threats in Indian Logistics: Preventing internal security risks
- Coming Next: The manpower crisis and its impact on security operations